Here’s A Quick Way To Solve A Tips About How To Get A Secure Phone Line

Burner apps let you create disposable phone numbers you can even reuse.
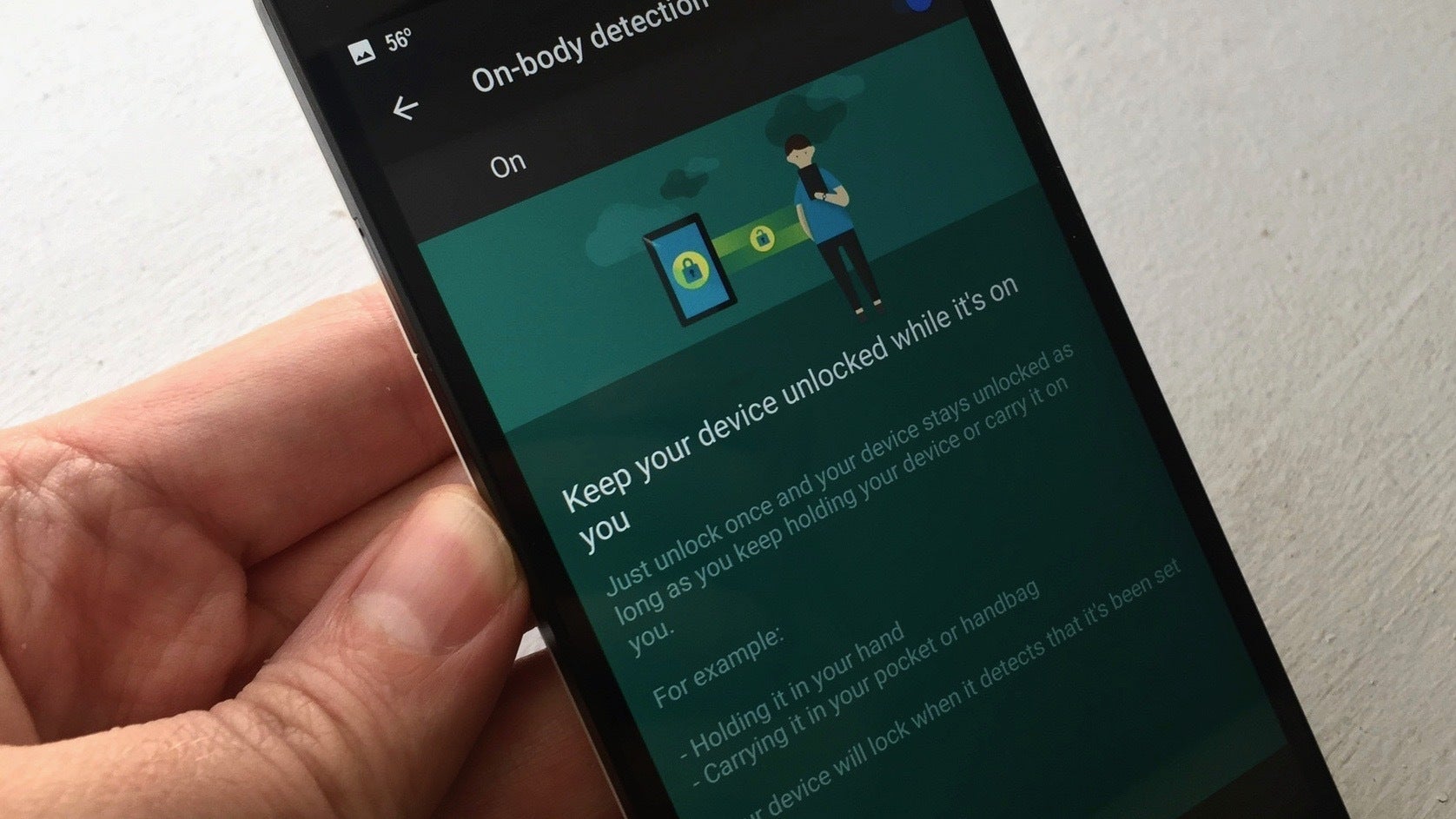
How to get a secure phone line. How to make your mobile phone safe and secure although hacking techniques can be complex, the measures to protect your phone don’t have to be. The first thing you want to do is make sure access. Rishi sunak is trying his best to get back on message after he was forced to suspend lee anderson for islamophobic comments about the london mayor.
You've probably granted countless apps access to parts of your google account over. How to secure your devices and accounts. Here’s what you need to know.
These are usually used in conjunction. Voip providers, such as zoom and skype,. They also come with some.
It’s best to choose something local so. Temporary phone numbers for verification receive sms online. How do you secure your mobile phone line for my business?
Cloudflare zero trust sim(enterprise) 6. Purchase a telephone encryption device like the secure phone miser, the pro encryption system or the secure line 700 (see resources). The best antivirus software can help keep your mobile phone protected from malware, ransomware attacks, and other cyber threats.
The most secure mobile providers for us residents are: Ever get the feeling you're being watched? Here’s greater detail about each of these.
Voice over internet protocol (voip) voip is a leading call communication standard that enables users to make voice and video calls. The best way to secure your mobile phone line for your business. A secure phone line is conceptually possible;
Quackr allows you to use a secure temporary phone number instead of your real phone. Only the people on a call are privy to the conversation. Silent phone(secure team communications) 5.
Once the app is finished downloading, tap it to open sideline. The app will ask your desired area code for your new number. When you don't want to hand out your digits, don't buy a separate phone.
While the signal can be intercepted by tapping into the physical line, as in some guy climbing up a telephone pole, the more modern method of intercepting land. Endpoint security phone security: There are a few steps you can take to secure your phone against malicious attacks and potential hacks.