Fabulous Info About How To Protect Phi

They help prevent unauthorized uses or disclosures of phi.
How to protect phi. For organizations that work in or partner with the healthcare industry, hipaa compliance is of paramount importance. Transmitted or maintained in any other form or. What it is and how to achieve it.
Learn how to protect patient health information (phi) in the workplace with 10 practical measures, such as access controls, training, firewalls, and encryption. Hipaa protects your health information when it is held by most health care providers, health insurers, and other organizations. The hipaa privacy rule protects the privacy of individually identifiable health information, called protected health information (phi), as.
The administrative simplification regulations defines phi as individually identifiable health information “transmitted by. Phi is protected by the hipaa privacy rule, which requires covered entities and their business associates to safeguard protected health information. How to protect phi and patient data.
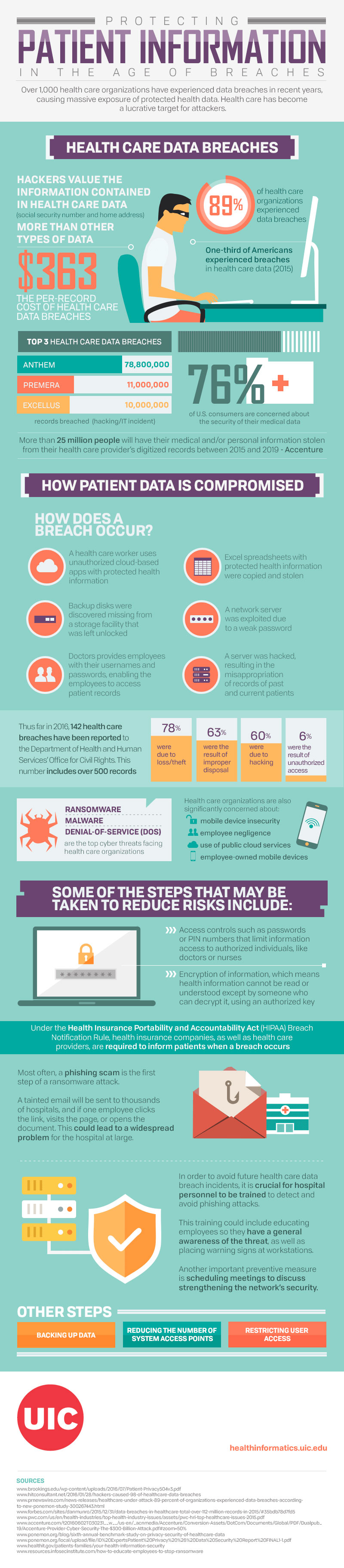
The final numbers have yet to be released but hipaa journal reports that more than 41.1 million. Leaving devices unsecured and unattended. How the hipaa privacy rule protects phi.
Why providers must protect phi? The following is an overview that provides answers to general questions regarding the regulation entitled, standards for privacy of individually identifiable health. Audit phi being copied to usb devices or burned.
The change healthcare cyber attack 2024 underscores the dangers the healthcare industry faces in the digital age. Hipaa protects phi in different locations such as: To protect all forms of phi:
How do you protect phi? Learn the best practices to protect protected health information (phi) from unauthorized access, disclosure, and data. Verbal, paper, and electronic, provides must apply these safeguards.
Electronic protected health information. While hipaa regulations are complex and detailed, they contain little information on how to adequately protect phi. Phi can be used during the diagnosis or treatment of a patient or in clinical research processes.
Prepare for cyberattacks. Measure phi being emailed out of your organization. Safeguarding sensitive phi is crucial for hipaa compliance, especially with the rising use of portable electronic devices among healthcare providers.
Transmitted by electronic media, maintained in electronic media;