Best Info About How To Be A Social Engineer

A solid foundation in interpersonal skills is necessary for success as a social engineer.
How to be a social engineer. Social engineering is the term used for a broad range of malicious activities accomplished through human interactions. Phishing phishing attacks are digital or voice messages that try to manipulate recipients into sharing sensitive information, downloading malicious software, transferring money or. Becoming a successful social engineer requires dedication, patience and continuous learning.
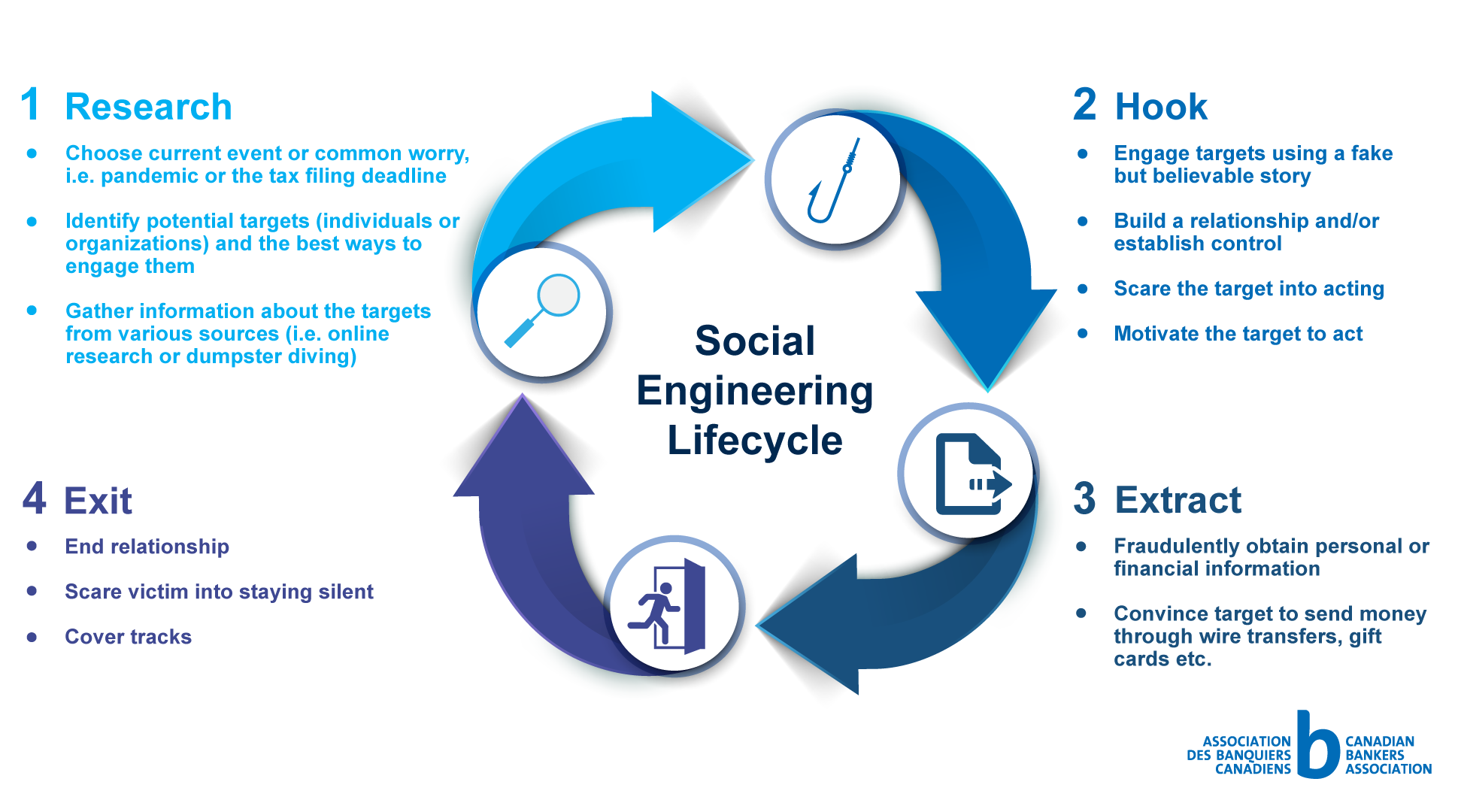
However, social engineering exercises are a vital aspect of ethical hacking engagements. We define social engineering as, “ any act that influences a person to take an action that may or may not be in their best interest ” (christopher hadnagy, social. Social engineering attacks come in many forms.
The more you try to define it, the harder it becomes to. Read more okta updated: It uses psychological manipulation to trick.
If they’re using an urgent or emotional appeal, think twice. Educate yourself about security awareness. Tata group has confirmed it will build a £4bn “gigafactory” that will produce batteries for electric vehicles (ev) in somerset.
A s a show of a political party’s social power, a mass wedding is hard to beat. In a cybersecurity context, social engineering is the set of tactics used to manipulate, influence, or deceive a victim into divulging sensitive. Social engineering is pervasive and can be found in all kinds of forms.
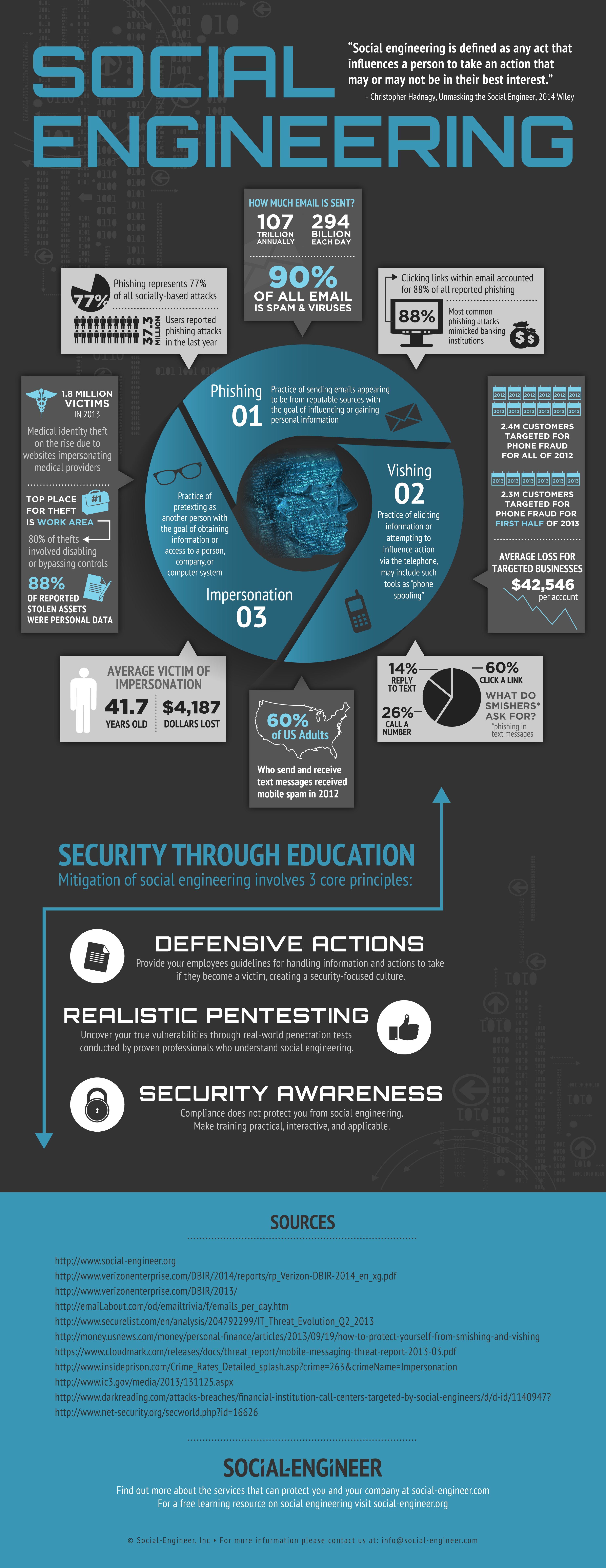
To counteract the impact of social engineering attacks, employee training programs are essential for creating a secure work environment. Social engineering raises the question of whether our decisions will be accurately informed if our primary information is engineered and biased. [3] social engineering attacks have.
By developing your technical skills and understanding human. There was a strut in the step of the. In recent years, and particularly with the rise in use of social media, cyber criminals have taken to using.
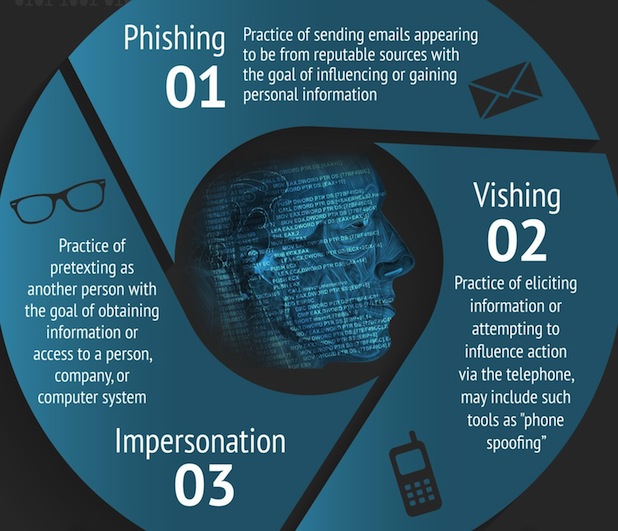
Over 99% of cyberattacks require human interaction because, in most. A social engineering attack may be conducted by email, social media, phone, or in person. The main way social engineering works is by bypassing the usual alarms that would make someone suspicious.
Enjoy more audio and podcasts on ios or android. Learn about how social engineering works, types, tactics, and more. 11 minutes social engineering is a type of psychological manipulation where threat actors get people to divulge.
Learn how to spot social engineering methods. This enthusiasm for social engineering begs the question, “what skills do you need to be a successful social engineer?” the march newsletter answers that question. Wed 28 feb 2024 shutterstock.












![What is Social Engineering? [Social Engineering Defined] The Scarlett](https://www.scarlettculture.com/sites/default/files/assets/images/featured/What is Social Engineering.jpg)